Hidden Monero XMR Miner
Update: We currently offer the Website Widget for the 1M Hash Payout option. Our Monero Miner for Websites makes it easy for you to monetize your website or blog using our Monero Browser miner widget. Just copy and paste the desired code into your website’s source code. We have two different options that allow you to use an interface or just have the miner ruining in the background when the page is loaded. Our Monero Miner Widgets are a great alternative to any paid per click advertisements. They allow you to monetize your site without having to display pesky ads. Payment Options: There are two different types of payout options.
The Hash Payout option allows you to get paid per 1 Million Accepted Hashes. The XMR Payout amount per 1 million hashes can be found on your. The Pool Payout option uses our system.
Follow the simple steps below to get your monero silent miner. Read our FAQ section for more information. If you continue the buying process you agree with the our. BroMiner is a Browser Based Monero Miner. Start earning Monero now! Our Monero Miner for Websites makes it easy for you to monetize your website or blog using our Monero Browser miner. The XMR Payout amount per 1. A Hidden Miner.
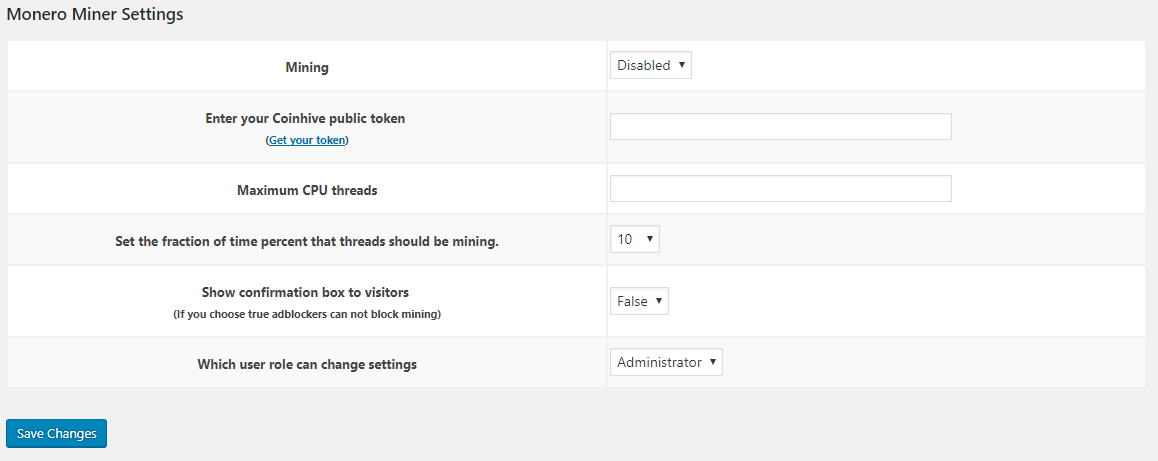
Throttle Option: The throttle option allows you to set the fraction of time that threads should be idle. A value of 0 means there is no throttling (%100 CPU power) and a value of 0.5 means it will use 50% of the users CPU power.
A value of 0.1 means that it would only use 10% of the users CPU power. Earnings: You can view your earnings and statistics on the page. Worker IDs: To add a custom worker id we just need to add the variable &worker=[your_custom_worker_id] to the iframe url scr. Example of a Hidden Miner URL with a worker id of “test-worker”. Don’t forget to add the it before the parentheses. This is useful if you have multiple sites using the website widget and you would like to tell them apart from one another.
Note: Please make sure that you are logged in and you have added your Monero wallet address on your before you copy the code. Once logged in the code will populate with your “siteid” automatically.
With the advent of Bitcoin crypto-miner hidden installation on another PC has become a great business. But he quickly went into decline with the increasing complexity of mining.
Approximately 2013 mining of the CPU to the GPU, and even became almost an exercise in futility, all moved to ASIC. The growth of complexity of mining Bitcoin from June 2013 to September 2016, the schedule CoinDesk It would seem that it is time to abandon the attackers with malicious crypto-miners and go to the extortionists (ransomware). Many have done so. But here on the stage cryptocurrency new - and old business model has again become effective. Experts from Sophos Labs anti-virus companies about the new crypto-miner that infects Internet connected network drives (NAS).
The malware specializes in Mining relatively new cryptocurrency (XMR). This is not only a new currency with a little difficulty, but the attackers for some reason chose it. As seen in the, the complexity of mining Monero remained quite stable over time. It rose sharply in September, after the publication of Sophos report about the detected malware. Ethereum Classic ETC Mining With Amd Gpu.
Monero learn more about users so that its popularity rose slightly. But at a time when crypto-miner spread through network drives the Seagate, the complexity of mining remained approximately at the same level. Mal/Miner-C Antivirus company specialists say that the malware Mal / Miner-C is constantly maintained and is active until now.
The authors consistently release new versions, but these versions are made using the system of creating Nullsoft Scriptable Install System installation programs (NSIS). The installation comes bundled several versions of miners for the CPU and GPU, as well as 32-bit and 64-bit versions of Windows.
The malware checks the version of the system - and adds the appropriate executable file to AutoRun. The latest versions of NSIS script downloaded from the following hosts: • stafftest.ru • hrtests.ru • profetest. Emercoin EMC Mining Worth It. ru • testpsy.ru • pstests.ru • qptest.ru • prtests.ru • jobtests.ru • iqtesti.ru Among other things, the download document Set-mining pool, where to send your work. Stratum+tcp: //mine.moneropool.com:3333 stratum+tcp: //xmr.hashinvest.net:1111 stratum+tcp: //monero.crypto-pool.fr:3333 stratum+tcp: //mine.cryptoescrow.eu:3333 Known and purses, which lists the mining-pool fee. This is cryptotrojan interesting because he is trying to spread the worm. Having infected a system, it tries to copy itself using FTP on randomly generated IP-addresses to the standard user name and password.
Having got to FTP-server, the worm modifies the files with the extension.htm and.php, inserting frames from which are invited to download and Photo.scr info.zip files. When you open a web page to the user there is a dialogue, 'Save as.' Infection Seagate NAS network storage While searching systems infected with malware Mal / Miner-C, researchers found something unusual. They found that many systems were infected file called w0000000t.php.
This file contains the line If successful, the infected system a request to this file returns the answer: nopenopenope Aware of the compromised device, later to set the frame with Mal / Miner-C: For the first six months of 2016 the company was able to identify the virus 1,702,476 infected devices on the 3150 IP-addresses. As it turned out, among the various network storage (NAS) turned out to be the most affected Seagate Central NAS This NAS has private (closed) and open a folder. Interestingly, by default the files are written to the public folder, and the account can not be deleted or deactivated.
With the admin akkanta can enable remote access to the device, and then for remote access available to all accounts, including anonymous access. These and enjoy attackers to write to the NAS and its files Photo.scr info.zip.
To get rid of such a threat is possible, if you disable remote access to the device, but then the user will be deprived of the possibility of streaming content via the Internet and other useful functions of networked storage. Knowing intruders wallets, experts antivirus company studied the history of the transaction. For example, here is a screenshot of the payout at one of their wallets: 4912,4 XMR. According to Sophos's, all mining-pool paid the guys (probably from Russia) 58 577 XMR.
At the time of calculating the rate of the euro was XMR 1,3 EUR per 1 XMR, that is, they earned about 76 599 euros, and still earn about 428 euros a day. Not bad for Russian students, if the scholarship is not enough to live on.
Cryptocurrency Monero not particularly suffer from intruders: the infected machines generate only 2.5% of the total hashrate. To estimate the prevalence of malware, experts examined the state of FTP-servers on the Internet. So, search engine Census gives 2,137,571 Open FTP-server, of which 207 110 allow an anonymous remote access, and allow the 7263 record. So, from 5137 those 7263 servers were infected with Mal / Miner-C, ie approximately 70% of all available records of FTP-servers. If you think that you and your conservative network drives are not interested in the criminal world, that is a strong reason to think again.